We already know that a certificate that contains a public key (PUB-K1) is sent in STEP 2 from the LinkedIn server to the client.
Today we will open the Blackbox that how this certificate is generated for the LinkedIn server.
How a Certificate is Signed?
Start from the very initial state. Let's say the LinkedIn server does not have a certificate and it wants to secure its website with HTTPS.
To generate a certificate from a trusted CA, LinkedIn has to generate a key pair first, public (PUB-K1) and private key (PRV-K1).
This key pair can be generated using different Asymmetric key/Public key cryptography algorithms, e.g. RSA, Diffie-Hellman, DSA, etc.

Fig: The server has a key pair
On the other hand, CA also should have a key pair — public key (say PUB-K2), and private key (say, PRV-K2).

Fig: The CA also has a key pair
Now with identification information and PUB-K1, the server will generate a Certificate Signing Request (CSR).
The server will send the CSR to a trusted CA to generate a certificate for that server.
After verifying all the information, the CA will generate a signed certificate for that server using its private key (PRV-K2) from the CSR.
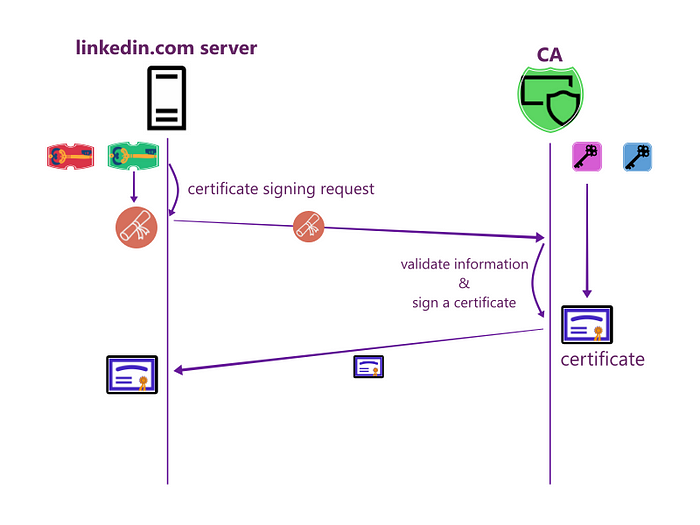
Fig: CA sign a certificate for the server
Now CA will send it to the server.
![HTTPS [EP 02] — How to Generate a Certificate?](https://cdn.hashnode.com/res/hashnode/image/upload/v1713114411314/5b74d16d-d14a-4010-91e3-c348af9b6a44.png?w=1600&h=840&fit=crop&crop=entropy&auto=compress,format&format=webp)